As part of our work in the EU-funded Allegro project, we investigated a machine learning-based attack on Physical Unclonable Function (PUF) systems using Generative Adversarial Networks (GANs).
➡️ We specifically used a Conditional GAN (cGAN) implemented through the Pix2Pix framework, designed to generate fake but passable speckle patterns based on challenge-response pairs (CRPs) from the system.
🛠️ How we did it:
- A U-Net-based Generator and a PatchGAN Discriminator were trained on 24,000 CRPs (out of 30,000 total), with 6,000 used for testing.
- The GAN was trained over 150 epochs, generating 150 models, each evaluated using cross-correlation with experimental data.
- The best-performing model was used to create 6000 speckle patterns, which were passed through the PUF authentication pipeline.
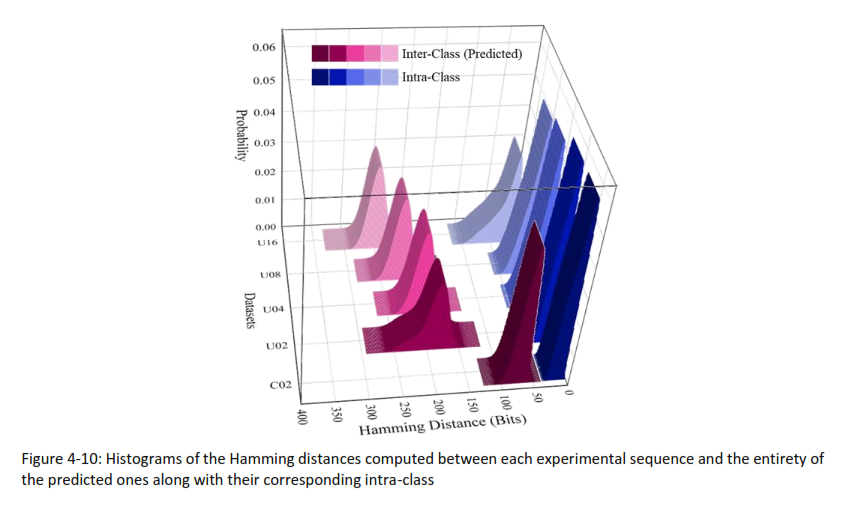
- Finally, we computed Hamming distances between enrolled and predicted responses to assess the attack’s effectiveness.
📌 This experiment highlights the security challenges posed by data-driven attacks, even when limited system knowledge is available to adversaries. The results help us evaluate the robustness of fuzzy extractors and CRP-based authentication against sophisticated AI attacks.
This effort pushes forward the understanding of adversarial capabilities in emerging authentication systems and supports the development of more resilient PUF-based security mechanisms.
#CyberSecurity #MachineLearning #GAN #PUF #Pix2Pix #Authentication #AllegroProject #AI #FuzzyExtractor #MLAttack #UML #EUProjects #AdversarialAI #EdgeSecurity